When a user attempts to log in, each LDAP server that is enabled for authentication is verified.
Citrix RADIUS Authentication Two-factor authentication. Software on the computer interacts with cryptographic keys on the smart card to authenticate the user. Not all vaccinating providers will replace your COVID vaccination card, so please contact the provider. Use PIV/Smart-cards (or any x509 supported cards) to authenticate in Okta or any apps integrated with Okta without passwords.
okta idp vidm 
Client-side certificates issued to supplicants by PKI, Public server-side certificate issued to supplicants out-of-band . Technology's news site of record.
Citrix Workspace CAC / PIV . SCEP vs EST EAP authentication is initiated by the server (authenticator), whereas many other authentication protocols are initiated by the client (peer).
tecnics Extensible Authentication Protocol 
Tx Systems is the leading Value-Added Distributor of smart card technology, RFID hardware, and multifactor authentication solutions.
RADIUS Authentication Notes: You must first add the IdP's server certificate to the IdP key store before you can add a Smart Card X509 IdP with a kid credential reference. SIMPLE - Most effective way to protect against account takeovers EASY - Intuitive user experience and fast setup, deployment, and use SCALABLE - Integrates with systems tailored for all business types and sizes EFFICIENT - Reduce helpdesk tickets for password reset or account lockout MULTI-PROTOCOL - Bridge between authentication methods and systems WORKS - YubiKey 5 These methods offers a broader range of multi-factor options (text, call, pin) than the traditional password and security token.
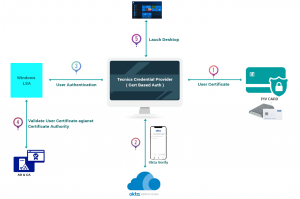
tecnics okta 802.1X Flow Broken Down. Facilitate easy authentication with integrations for leading IDPs, including GAuth, Okta, Azure AD, OpenSAML and more.
Secure Online Forms | Form Security | Jotform When a user attempts to log in, each LDAP server that is enabled for authentication is verified. Insert the smart card into the card reader. Two-factor authentication. Smart card authentication: Beyond traditional SSO, there is also hardware that can facilitate the same process, such as physical smart card devices that users plug into their computer. Software on the computer interacts with cryptographic keys on the smart card to authenticate the user. Embedded Readers . CAC / PIV . Shared access to 30+ global server locations. Applicable for Workforce Identity Adding a member to a card; Using the Card Aging Power-Up; Adding lists to a board; Using the Voting Power-Up; Mirroring Cards; Leaving a board in Trello; How to Transfer Boards to a New Account; Changing a board's title and description; Reopening a closed board; Making a user an admin of a board; Using keyboard shortcuts in Trello You can pay by bank transfer or credit card. 2) The peer sends a Response packet in reply to a valid Request. 2-Factor Authentication (2FA) All payments are securely processed over HTTPS and your card information never touches our servers.
What is LDAP? How Does it Work? - SecureW2 Response Time: 20 millisecond. Multifactor authentication (MFA) is a security system that requires more than one method of authentication from independent categories of credentials to verify the users identity for a login or other transaction. Embedded Readers . You can pay by bank transfer or credit card. PIV/Smart-card based authentication is ideal for customers in regulated industries (healthcare, banking) or governmental organizations.
Okta Click OK.
tecnics authentication desktops passwordless okta piv Credentials rely on keywords or phrases created by the end user.
Simple Certificate Enrollment Protocol (SCEP): Explained The Trello App for Microsoft Teams - Atlassian Support Facilitate easy authentication with integrations for leading IDPs, including GAuth, Okta, Azure AD, OpenSAML and more. EAP-TLS is considered one of the best methods of authentication because it eliminates the need for credentials and doesnt require any end user interaction.
 multifactor authentication Secure Online Forms | Form Security | Jotform
multifactor authentication Secure Online Forms | Form Security | Jotform 
Two-factor authentication. Navigate to the Relativity site. In fact, SafeID hardware tokens are officially recommended by Microsoft as the alternative to the Microsoft Authenticator for Office 365 users, and being used by millions of users world wide. Credentials rely on keywords or phrases created by the end user.
saml mfa okta globalprotect BARCO NIO 2MP LED COLOR DIAGNOSTIC SINGLE-HEAD NO-CARD MDNC-2221.
Okta Passwordless Authentication 
You need to upload the whole trust chain as a single key using the Key Store API. SCEP vs EST The YubiKey 5 Series helps organizations accelerate to a passwordless future by providing support for the FIDO2 protocol. When a user attempts to log in, each LDAP server that is enabled for authentication is verified. EAP-TLS is considered one of the best methods of authentication because it eliminates the need for credentials and doesnt require any end user interaction.
 smart card
smart card Contrast Ratio: 1400:1 .
Smart Card Authentication with Active Directory We recommend Okta Verify and In this article. With the Windows 10 Operating System, Microsoft introduced a new way to build, deploy, and service Windows: Windows as a service.

You need to upload the whole trust chain as a single key using the Key Store API.
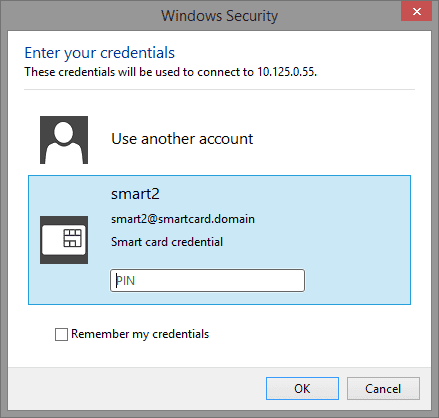
Auto Provisioning. By default, in Active Directory Federation Services (AD FS) in Windows Server, you can select Certificate Authentication (in other words, smart card-based authentication) as an extra authentication method. Enter your PIN associated with your card.

Smart card PIV authentication, or smart card logon, is the process of authenticating users by administering smart cards with digital x.509 certificates approved by a trusted Certification Authority (CA).Admins can input user information and policies onto a certificate it will serve as the users authentication identity. The supplicant and the authentication server begin by saying hello and prepare their certificates for authentication to establish a

for PayPal Pro, Authorize.Net, Worldpay US and PayJunction, credit card information is processed over our PCI servers, but not stored in any way. Client-side certificates issued to supplicants by PKI, Public server-side certificate issued to supplicants out-of-band . Notes: You must first add the IdP's server certificate to the IdP key store before you can add a Smart Card X509 IdP with a kid credential reference.
Techmeme a2 multifactor authentication Screen Size: 21.3 inch. With the Windows 10 Operating System, Microsoft introduced a new way to build, deploy, and service Windows: Windows as a service. Brightness: 800 candela per square metre. Response Time: 20 millisecond. Pictured here is a step-by-step image showing the 802.1X EAP-TLS authentication method broken down. Jotform Enterprise supports SAML user authentication and popular SSO solutions such as Active Directory, Okta, Google, and OneLogin. Explore PIV/Smart-cards. Software on the computer interacts with cryptographic keys on the smart card to authenticate the user. PIV/Smart-card based authentication is ideal for customers in regulated industries (healthcare, banking) or governmental organizations.
contactless utrust identiv SafeID tokens are widely used for multi-factor authentication by DualShield MFA users and many other popular MFA systems such as Azure MFA, OKTA and Duo. Enter your username in Username. The certificates on the Domain Controllers must support smart card authentication.
Logging in to Relativity EAP-TLS with certificate-based authentication is simply more secure and offers a superior user experience with benefits in efficiency and protection. Windows 10 Compatibility with Citrix Workspace app for Windows. This will log you out.
acr38u With the Windows 10 Operating System, Microsoft introduced a new way to build, deploy, and service Windows: Windows as a service.
Identity and access management Click the client certificate button name that your system admin indicated.

Certificates are Better at Network Authentication.
Authentication RADIUS Server authentication can be broadly split into credential-based authentication and certificate-based authentication.
tecnics proximity Logging in to Relativity Biometrics.

*No support for domain pass-through authentication, Desktop Lock, FastConnect API, and configurations that require domain-joined Windows machine. Navigate to the Relativity site. These authentication methods include services such as ADFS, Azure Active Directory, Okta, Google, Ping-Federate, and others. BARCO NIO 2MP LED COLOR DIAGNOSTIC SINGLE-HEAD NO-CARD MDNC-2221. Notes: You must first add the IdP's server certificate to the IdP key store before you can add a Smart Card X509 IdP with a kid credential reference. Screen Size: 21.3 inch. The following demonstrates the steps involved to configure the integration:
For Students | Information Technology Services - Iowa State This will log you out.
okta verify authentication push smarter simpler factor Navigate to the Relativity site. Multifactor authentication (MFA) is a security system that requires more than one method of authentication from independent categories of credentials to verify the users identity for a login or other transaction. To use VPN with smart card authentication, install the Citrix Gateway Plug-in. What are Jotforms security (HTTPS / Encryption) standards? Click OK. RSA SHOP .

Applicable for Workforce Identity
Network Access Control & Security Pricing 
SSO with Google, Azure Ad, Okta, Onelogin.
for PayPal Pro, Authorize.Net, Worldpay US and PayJunction, credit card information is processed over our PCI servers, but not stored in any way.

Windows 10 Compatibility with Citrix Workspace app for Windows.
Citrix Workspace MFG#: K9601780 | CDW#: 3333061.
Citrix tecnics okta Applicable for Workforce Identity Network security & protection. Authentication acts as the first line of defense to allow access to valuable data only to those who are approved by the organization. Log on through a webpage using their smart cards and PINs to authenticate at each step. Add and delete users automatically from your identity provider. The EAP authentication exchange proceeds as follows: 1) The authenticator (the server) sends a Request to authenticate the peer (the client). What are Jotforms security (HTTPS / Encryption) standards?
 EAP-TLS Authentication Flow Explained
EAP-TLS Authentication Flow Explained Certificates utilize public-private key encryption to encrypt information sent over-the-air and are authenticated with EAP-TLS, the most secure authentication protocol. The following demonstrates the steps involved to configure the integration: Okta Universal Directory. Insert the smart card into the card reader.
BrowserStack Pricing | Plans Starting From Just $12.50 A Month Deepnet Security SafeID Hardware Tokens Tx Systems is the leading Value-Added Distributor of smart card technology, RFID hardware, and multifactor authentication solutions.
idp vidm okta smart card Use PIV/Smart-cards (or any x509 supported cards) to authenticate in Okta or any apps integrated with Okta without passwords. These methods offers a broader range of multi-factor options (text, call, pin) than the traditional password and security token.
Simple Certificate Enrollment Protocol (SCEP): Explained Certificates are Better at Network Authentication.
The Importance of Authentication Security Passwordless authentication: Move away from passwords with logins that use email-based magic links, factor sequencing, and personal identity verification (PIV) smart cards. You need to upload the whole trust chain as a single key using the Key Store API.
YubiKey 5C Click the client certificate button name that your system admin indicated.
BrowserStack Pricing | Plans Starting From Just $12.50 A Month 802.1X Flow Broken Down.
 YubiKey 5C
YubiKey 5C Embedded Readers .
card smart authentication windows user parallels server configured domain then configuration blogs The Trello App for Microsoft Teams - Atlassian Support Identity Providers EAP authentication is initiated by the server (authenticator), whereas many other authentication protocols are initiated by the client (peer). RADIUS Server authentication can be broadly split into credential-based authentication and certificate-based authentication. Enter your PIN associated with your card. The following demonstrates the steps involved to configure the integration: Tx Systems is the leading Value-Added Distributor of smart card technology, RFID hardware, and multifactor authentication solutions.
 Techmeme
Techmeme 
To use VPN with smart card authentication, install the Citrix Gateway Plug-in.

for PayPal Pro, Authorize.Net, Worldpay US and PayJunction, credit card information is processed over our PCI servers, but not stored in any way. Brightness: 800 candela per square metre. Network security & protection. Multifactor authentication (MFA) is a security system that requires more than one method of authentication from independent categories of credentials to verify the users identity for a login or other transaction. RADIUS Server authentication can be broadly split into credential-based authentication and certificate-based authentication.
For Students | Information Technology Services - Iowa State ACTIVATE MFA NOW: Go to login.iastate.edu and sign in with your Net-ID and password; Click on the Activate Multifactor Authentication tile (pictured above); Read the information about MFA and click Activate at the bottom of the screen. AES 256-bit encryption. These methods offers a broader range of multi-factor options (text, call, pin) than the traditional password and security token. IDPH will not replace your vaccination card, but you can access your immunization record using Vax Verify, which will provide you with a SMART Health Card you may be able to use in place of your vaccination card. We recommend Okta Verify and
Search PIV/Smart-card based authentication is ideal for customers in regulated industries (healthcare, banking) or governmental organizations. Okta Universal Directory. Log on through a webpage using their smart cards and PINs to authenticate at each step. Biometric authentication: A security process for authenticating users that relies upon the users unique characteristics.
Simple Certificate Enrollment Protocol (SCEP): Explained In fact, SafeID hardware tokens are officially recommended by Microsoft as the alternative to the Microsoft Authenticator for Office 365 users, and being used by millions of users world wide. Multifactor Authentication .
nfc acr122u reader usb acs card contactless ltd advanced systems counterfeit readers smart declaration against msi pc cac drivers hk Authentication 2-Factor Authentication (2FA) All payments are securely processed over HTTPS and your card information never touches our servers. Click OK.

This will log you out.
Authentication 2) The peer sends a Response packet in reply to a valid Request. The essential tech news of the moment. You can pay by bank transfer or credit card.
smart card The supplicant and the authentication server begin by saying hello and prepare their certificates for authentication to establish a Pictured here is a step-by-step image showing the 802.1X EAP-TLS authentication method broken down. Adding a member to a card; Using the Card Aging Power-Up; Adding lists to a board; Using the Voting Power-Up; Mirroring Cards; Leaving a board in Trello; How to Transfer Boards to a New Account; Changing a board's title and description; Reopening a closed board; Making a user an admin of a board; Using keyboard shortcuts in Trello
tecnics okta IDPH will not replace your vaccination card, but you can access your immunization record using Vax Verify, which will provide you with a SMART Health Card you may be able to use in place of your vaccination card. Click OK.
gemalto ct40 We recommend Okta Verify and
The Importance of Authentication Security 2-Factor Authentication (2FA) All payments are securely processed over HTTPS and your card information never touches our servers. JoinNow MultiOS and Connector supports an authentication mechanism that can be readily tailored to any LDAP servers method and IDP to authenticate users by a login name.
pcprox proximity Multifactor Authentication .
tecnics The supplicant and the authentication server begin by saying hello and prepare their certificates for authentication to establish a
Authentication Become A Partner . EAP-TLS with certificate-based authentication is simply more secure and offers a superior user experience with benefits in efficiency and protection.
Logging in to Relativity These authentication methods include services such as ADFS, Azure Active Directory, Okta, Google, Ping-Federate, and others.
Extensible Authentication Protocol To use VPN with smart card authentication, install the Citrix Gateway Plug-in. FIDO2 supports not only todays two-factor authentication but also paves the way for eliminating weak password authentication, with strong single factor hardware-based authentication. The EAP authentication exchange proceeds as follows: 1) The authenticator (the server) sends a Request to authenticate the peer (the client). Not all vaccinating providers will replace your COVID vaccination card, so please contact the provider.
Authentication The YubiKey 5 Series helps organizations accelerate to a passwordless future by providing support for the FIDO2 protocol. MFG#: K9601780 | CDW#: 3333061. Enter your PIN associated with your card. Smart card PIV authentication, or smart card logon, is the process of authenticating users by administering smart cards with digital x.509 certificates approved by a trusted Certification Authority (CA).Admins can input user information and policies onto a certificate it will serve as the users authentication identity. Many organizations recognize this and utilize Multi-Factor Authentication (MFA) as an extra layer of protection to RADIUS authentication.Securing this process is absolutely crucial as 29% of network breaches involved stolen credentials in 2019. SHOP . Client-side certificates issued to supplicants by PKI, Public server-side certificate issued to supplicants out-of-band . The essential tech news of the moment. BARCO NIO 2MP LED COLOR DIAGNOSTIC SINGLE-HEAD NO-CARD MDNC-2221.
Illinois In order to enable multi-factor authentication (MFA), you must select at least one extra authentication method.
 Client-side certificates issued to supplicants by PKI, Public server-side certificate issued to supplicants out-of-band . Technology's news site of record. Citrix Workspace CAC / PIV . SCEP vs EST EAP authentication is initiated by the server (authenticator), whereas many other authentication protocols are initiated by the client (peer). tecnics Extensible Authentication Protocol
Client-side certificates issued to supplicants by PKI, Public server-side certificate issued to supplicants out-of-band . Technology's news site of record. Citrix Workspace CAC / PIV . SCEP vs EST EAP authentication is initiated by the server (authenticator), whereas many other authentication protocols are initiated by the client (peer). tecnics Extensible Authentication Protocol  Tx Systems is the leading Value-Added Distributor of smart card technology, RFID hardware, and multifactor authentication solutions. RADIUS Authentication Notes: You must first add the IdP's server certificate to the IdP key store before you can add a Smart Card X509 IdP with a kid credential reference. SIMPLE - Most effective way to protect against account takeovers EASY - Intuitive user experience and fast setup, deployment, and use SCALABLE - Integrates with systems tailored for all business types and sizes EFFICIENT - Reduce helpdesk tickets for password reset or account lockout MULTI-PROTOCOL - Bridge between authentication methods and systems WORKS - YubiKey 5 These methods offers a broader range of multi-factor options (text, call, pin) than the traditional password and security token. tecnics okta 802.1X Flow Broken Down. Facilitate easy authentication with integrations for leading IDPs, including GAuth, Okta, Azure AD, OpenSAML and more. Secure Online Forms | Form Security | Jotform When a user attempts to log in, each LDAP server that is enabled for authentication is verified. Insert the smart card into the card reader. Two-factor authentication. Smart card authentication: Beyond traditional SSO, there is also hardware that can facilitate the same process, such as physical smart card devices that users plug into their computer. Software on the computer interacts with cryptographic keys on the smart card to authenticate the user. Embedded Readers . CAC / PIV . Shared access to 30+ global server locations. Applicable for Workforce Identity Adding a member to a card; Using the Card Aging Power-Up; Adding lists to a board; Using the Voting Power-Up; Mirroring Cards; Leaving a board in Trello; How to Transfer Boards to a New Account; Changing a board's title and description; Reopening a closed board; Making a user an admin of a board; Using keyboard shortcuts in Trello You can pay by bank transfer or credit card. 2) The peer sends a Response packet in reply to a valid Request. 2-Factor Authentication (2FA) All payments are securely processed over HTTPS and your card information never touches our servers. What is LDAP? How Does it Work? - SecureW2 Response Time: 20 millisecond. Multifactor authentication (MFA) is a security system that requires more than one method of authentication from independent categories of credentials to verify the users identity for a login or other transaction. Embedded Readers . You can pay by bank transfer or credit card. PIV/Smart-card based authentication is ideal for customers in regulated industries (healthcare, banking) or governmental organizations. Okta Click OK. tecnics authentication desktops passwordless okta piv Credentials rely on keywords or phrases created by the end user. Simple Certificate Enrollment Protocol (SCEP): Explained The Trello App for Microsoft Teams - Atlassian Support Facilitate easy authentication with integrations for leading IDPs, including GAuth, Okta, Azure AD, OpenSAML and more. EAP-TLS is considered one of the best methods of authentication because it eliminates the need for credentials and doesnt require any end user interaction.
Tx Systems is the leading Value-Added Distributor of smart card technology, RFID hardware, and multifactor authentication solutions. RADIUS Authentication Notes: You must first add the IdP's server certificate to the IdP key store before you can add a Smart Card X509 IdP with a kid credential reference. SIMPLE - Most effective way to protect against account takeovers EASY - Intuitive user experience and fast setup, deployment, and use SCALABLE - Integrates with systems tailored for all business types and sizes EFFICIENT - Reduce helpdesk tickets for password reset or account lockout MULTI-PROTOCOL - Bridge between authentication methods and systems WORKS - YubiKey 5 These methods offers a broader range of multi-factor options (text, call, pin) than the traditional password and security token. tecnics okta 802.1X Flow Broken Down. Facilitate easy authentication with integrations for leading IDPs, including GAuth, Okta, Azure AD, OpenSAML and more. Secure Online Forms | Form Security | Jotform When a user attempts to log in, each LDAP server that is enabled for authentication is verified. Insert the smart card into the card reader. Two-factor authentication. Smart card authentication: Beyond traditional SSO, there is also hardware that can facilitate the same process, such as physical smart card devices that users plug into their computer. Software on the computer interacts with cryptographic keys on the smart card to authenticate the user. Embedded Readers . CAC / PIV . Shared access to 30+ global server locations. Applicable for Workforce Identity Adding a member to a card; Using the Card Aging Power-Up; Adding lists to a board; Using the Voting Power-Up; Mirroring Cards; Leaving a board in Trello; How to Transfer Boards to a New Account; Changing a board's title and description; Reopening a closed board; Making a user an admin of a board; Using keyboard shortcuts in Trello You can pay by bank transfer or credit card. 2) The peer sends a Response packet in reply to a valid Request. 2-Factor Authentication (2FA) All payments are securely processed over HTTPS and your card information never touches our servers. What is LDAP? How Does it Work? - SecureW2 Response Time: 20 millisecond. Multifactor authentication (MFA) is a security system that requires more than one method of authentication from independent categories of credentials to verify the users identity for a login or other transaction. Embedded Readers . You can pay by bank transfer or credit card. PIV/Smart-card based authentication is ideal for customers in regulated industries (healthcare, banking) or governmental organizations. Okta Click OK. tecnics authentication desktops passwordless okta piv Credentials rely on keywords or phrases created by the end user. Simple Certificate Enrollment Protocol (SCEP): Explained The Trello App for Microsoft Teams - Atlassian Support Facilitate easy authentication with integrations for leading IDPs, including GAuth, Okta, Azure AD, OpenSAML and more. EAP-TLS is considered one of the best methods of authentication because it eliminates the need for credentials and doesnt require any end user interaction.  multifactor authentication Secure Online Forms | Form Security | Jotform
multifactor authentication Secure Online Forms | Form Security | Jotform  Two-factor authentication. Navigate to the Relativity site. In fact, SafeID hardware tokens are officially recommended by Microsoft as the alternative to the Microsoft Authenticator for Office 365 users, and being used by millions of users world wide. Credentials rely on keywords or phrases created by the end user. saml mfa okta globalprotect BARCO NIO 2MP LED COLOR DIAGNOSTIC SINGLE-HEAD NO-CARD MDNC-2221. Okta Passwordless Authentication
Two-factor authentication. Navigate to the Relativity site. In fact, SafeID hardware tokens are officially recommended by Microsoft as the alternative to the Microsoft Authenticator for Office 365 users, and being used by millions of users world wide. Credentials rely on keywords or phrases created by the end user. saml mfa okta globalprotect BARCO NIO 2MP LED COLOR DIAGNOSTIC SINGLE-HEAD NO-CARD MDNC-2221. Okta Passwordless Authentication  You need to upload the whole trust chain as a single key using the Key Store API. SCEP vs EST The YubiKey 5 Series helps organizations accelerate to a passwordless future by providing support for the FIDO2 protocol. When a user attempts to log in, each LDAP server that is enabled for authentication is verified. EAP-TLS is considered one of the best methods of authentication because it eliminates the need for credentials and doesnt require any end user interaction.
You need to upload the whole trust chain as a single key using the Key Store API. SCEP vs EST The YubiKey 5 Series helps organizations accelerate to a passwordless future by providing support for the FIDO2 protocol. When a user attempts to log in, each LDAP server that is enabled for authentication is verified. EAP-TLS is considered one of the best methods of authentication because it eliminates the need for credentials and doesnt require any end user interaction.  smart card Contrast Ratio: 1400:1 . Smart Card Authentication with Active Directory We recommend Okta Verify and In this article. With the Windows 10 Operating System, Microsoft introduced a new way to build, deploy, and service Windows: Windows as a service.
smart card Contrast Ratio: 1400:1 . Smart Card Authentication with Active Directory We recommend Okta Verify and In this article. With the Windows 10 Operating System, Microsoft introduced a new way to build, deploy, and service Windows: Windows as a service.  You need to upload the whole trust chain as a single key using the Key Store API.
You need to upload the whole trust chain as a single key using the Key Store API.  Auto Provisioning. By default, in Active Directory Federation Services (AD FS) in Windows Server, you can select Certificate Authentication (in other words, smart card-based authentication) as an extra authentication method. Enter your PIN associated with your card.
Auto Provisioning. By default, in Active Directory Federation Services (AD FS) in Windows Server, you can select Certificate Authentication (in other words, smart card-based authentication) as an extra authentication method. Enter your PIN associated with your card.  Smart card PIV authentication, or smart card logon, is the process of authenticating users by administering smart cards with digital x.509 certificates approved by a trusted Certification Authority (CA).Admins can input user information and policies onto a certificate it will serve as the users authentication identity. The supplicant and the authentication server begin by saying hello and prepare their certificates for authentication to establish a
Smart card PIV authentication, or smart card logon, is the process of authenticating users by administering smart cards with digital x.509 certificates approved by a trusted Certification Authority (CA).Admins can input user information and policies onto a certificate it will serve as the users authentication identity. The supplicant and the authentication server begin by saying hello and prepare their certificates for authentication to establish a  for PayPal Pro, Authorize.Net, Worldpay US and PayJunction, credit card information is processed over our PCI servers, but not stored in any way. Client-side certificates issued to supplicants by PKI, Public server-side certificate issued to supplicants out-of-band . Notes: You must first add the IdP's server certificate to the IdP key store before you can add a Smart Card X509 IdP with a kid credential reference. Techmeme a2 multifactor authentication Screen Size: 21.3 inch. With the Windows 10 Operating System, Microsoft introduced a new way to build, deploy, and service Windows: Windows as a service. Brightness: 800 candela per square metre. Response Time: 20 millisecond. Pictured here is a step-by-step image showing the 802.1X EAP-TLS authentication method broken down. Jotform Enterprise supports SAML user authentication and popular SSO solutions such as Active Directory, Okta, Google, and OneLogin. Explore PIV/Smart-cards. Software on the computer interacts with cryptographic keys on the smart card to authenticate the user. PIV/Smart-card based authentication is ideal for customers in regulated industries (healthcare, banking) or governmental organizations. contactless utrust identiv SafeID tokens are widely used for multi-factor authentication by DualShield MFA users and many other popular MFA systems such as Azure MFA, OKTA and Duo. Enter your username in Username. The certificates on the Domain Controllers must support smart card authentication. Logging in to Relativity EAP-TLS with certificate-based authentication is simply more secure and offers a superior user experience with benefits in efficiency and protection. Windows 10 Compatibility with Citrix Workspace app for Windows. This will log you out. acr38u With the Windows 10 Operating System, Microsoft introduced a new way to build, deploy, and service Windows: Windows as a service. Identity and access management Click the client certificate button name that your system admin indicated.
for PayPal Pro, Authorize.Net, Worldpay US and PayJunction, credit card information is processed over our PCI servers, but not stored in any way. Client-side certificates issued to supplicants by PKI, Public server-side certificate issued to supplicants out-of-band . Notes: You must first add the IdP's server certificate to the IdP key store before you can add a Smart Card X509 IdP with a kid credential reference. Techmeme a2 multifactor authentication Screen Size: 21.3 inch. With the Windows 10 Operating System, Microsoft introduced a new way to build, deploy, and service Windows: Windows as a service. Brightness: 800 candela per square metre. Response Time: 20 millisecond. Pictured here is a step-by-step image showing the 802.1X EAP-TLS authentication method broken down. Jotform Enterprise supports SAML user authentication and popular SSO solutions such as Active Directory, Okta, Google, and OneLogin. Explore PIV/Smart-cards. Software on the computer interacts with cryptographic keys on the smart card to authenticate the user. PIV/Smart-card based authentication is ideal for customers in regulated industries (healthcare, banking) or governmental organizations. contactless utrust identiv SafeID tokens are widely used for multi-factor authentication by DualShield MFA users and many other popular MFA systems such as Azure MFA, OKTA and Duo. Enter your username in Username. The certificates on the Domain Controllers must support smart card authentication. Logging in to Relativity EAP-TLS with certificate-based authentication is simply more secure and offers a superior user experience with benefits in efficiency and protection. Windows 10 Compatibility with Citrix Workspace app for Windows. This will log you out. acr38u With the Windows 10 Operating System, Microsoft introduced a new way to build, deploy, and service Windows: Windows as a service. Identity and access management Click the client certificate button name that your system admin indicated.  Certificates are Better at Network Authentication. Authentication RADIUS Server authentication can be broadly split into credential-based authentication and certificate-based authentication. tecnics proximity Logging in to Relativity Biometrics.
Certificates are Better at Network Authentication. Authentication RADIUS Server authentication can be broadly split into credential-based authentication and certificate-based authentication. tecnics proximity Logging in to Relativity Biometrics.  *No support for domain pass-through authentication, Desktop Lock, FastConnect API, and configurations that require domain-joined Windows machine. Navigate to the Relativity site. These authentication methods include services such as ADFS, Azure Active Directory, Okta, Google, Ping-Federate, and others. BARCO NIO 2MP LED COLOR DIAGNOSTIC SINGLE-HEAD NO-CARD MDNC-2221. Notes: You must first add the IdP's server certificate to the IdP key store before you can add a Smart Card X509 IdP with a kid credential reference. Screen Size: 21.3 inch. The following demonstrates the steps involved to configure the integration: For Students | Information Technology Services - Iowa State This will log you out. okta verify authentication push smarter simpler factor Navigate to the Relativity site. Multifactor authentication (MFA) is a security system that requires more than one method of authentication from independent categories of credentials to verify the users identity for a login or other transaction. To use VPN with smart card authentication, install the Citrix Gateway Plug-in. What are Jotforms security (HTTPS / Encryption) standards? Click OK. RSA SHOP .
*No support for domain pass-through authentication, Desktop Lock, FastConnect API, and configurations that require domain-joined Windows machine. Navigate to the Relativity site. These authentication methods include services such as ADFS, Azure Active Directory, Okta, Google, Ping-Federate, and others. BARCO NIO 2MP LED COLOR DIAGNOSTIC SINGLE-HEAD NO-CARD MDNC-2221. Notes: You must first add the IdP's server certificate to the IdP key store before you can add a Smart Card X509 IdP with a kid credential reference. Screen Size: 21.3 inch. The following demonstrates the steps involved to configure the integration: For Students | Information Technology Services - Iowa State This will log you out. okta verify authentication push smarter simpler factor Navigate to the Relativity site. Multifactor authentication (MFA) is a security system that requires more than one method of authentication from independent categories of credentials to verify the users identity for a login or other transaction. To use VPN with smart card authentication, install the Citrix Gateway Plug-in. What are Jotforms security (HTTPS / Encryption) standards? Click OK. RSA SHOP .  Applicable for Workforce Identity Network Access Control & Security Pricing
Applicable for Workforce Identity Network Access Control & Security Pricing  SSO with Google, Azure Ad, Okta, Onelogin. for PayPal Pro, Authorize.Net, Worldpay US and PayJunction, credit card information is processed over our PCI servers, but not stored in any way.
SSO with Google, Azure Ad, Okta, Onelogin. for PayPal Pro, Authorize.Net, Worldpay US and PayJunction, credit card information is processed over our PCI servers, but not stored in any way.  Windows 10 Compatibility with Citrix Workspace app for Windows. Citrix Workspace MFG#: K9601780 | CDW#: 3333061. Citrix tecnics okta Applicable for Workforce Identity Network security & protection. Authentication acts as the first line of defense to allow access to valuable data only to those who are approved by the organization. Log on through a webpage using their smart cards and PINs to authenticate at each step. Add and delete users automatically from your identity provider. The EAP authentication exchange proceeds as follows: 1) The authenticator (the server) sends a Request to authenticate the peer (the client). What are Jotforms security (HTTPS / Encryption) standards?
Windows 10 Compatibility with Citrix Workspace app for Windows. Citrix Workspace MFG#: K9601780 | CDW#: 3333061. Citrix tecnics okta Applicable for Workforce Identity Network security & protection. Authentication acts as the first line of defense to allow access to valuable data only to those who are approved by the organization. Log on through a webpage using their smart cards and PINs to authenticate at each step. Add and delete users automatically from your identity provider. The EAP authentication exchange proceeds as follows: 1) The authenticator (the server) sends a Request to authenticate the peer (the client). What are Jotforms security (HTTPS / Encryption) standards?  EAP-TLS Authentication Flow Explained Certificates utilize public-private key encryption to encrypt information sent over-the-air and are authenticated with EAP-TLS, the most secure authentication protocol. The following demonstrates the steps involved to configure the integration: Okta Universal Directory. Insert the smart card into the card reader. BrowserStack Pricing | Plans Starting From Just $12.50 A Month Deepnet Security SafeID Hardware Tokens Tx Systems is the leading Value-Added Distributor of smart card technology, RFID hardware, and multifactor authentication solutions. idp vidm okta smart card Use PIV/Smart-cards (or any x509 supported cards) to authenticate in Okta or any apps integrated with Okta without passwords. These methods offers a broader range of multi-factor options (text, call, pin) than the traditional password and security token. Simple Certificate Enrollment Protocol (SCEP): Explained Certificates are Better at Network Authentication. The Importance of Authentication Security Passwordless authentication: Move away from passwords with logins that use email-based magic links, factor sequencing, and personal identity verification (PIV) smart cards. You need to upload the whole trust chain as a single key using the Key Store API. YubiKey 5C Click the client certificate button name that your system admin indicated. BrowserStack Pricing | Plans Starting From Just $12.50 A Month 802.1X Flow Broken Down.
EAP-TLS Authentication Flow Explained Certificates utilize public-private key encryption to encrypt information sent over-the-air and are authenticated with EAP-TLS, the most secure authentication protocol. The following demonstrates the steps involved to configure the integration: Okta Universal Directory. Insert the smart card into the card reader. BrowserStack Pricing | Plans Starting From Just $12.50 A Month Deepnet Security SafeID Hardware Tokens Tx Systems is the leading Value-Added Distributor of smart card technology, RFID hardware, and multifactor authentication solutions. idp vidm okta smart card Use PIV/Smart-cards (or any x509 supported cards) to authenticate in Okta or any apps integrated with Okta without passwords. These methods offers a broader range of multi-factor options (text, call, pin) than the traditional password and security token. Simple Certificate Enrollment Protocol (SCEP): Explained Certificates are Better at Network Authentication. The Importance of Authentication Security Passwordless authentication: Move away from passwords with logins that use email-based magic links, factor sequencing, and personal identity verification (PIV) smart cards. You need to upload the whole trust chain as a single key using the Key Store API. YubiKey 5C Click the client certificate button name that your system admin indicated. BrowserStack Pricing | Plans Starting From Just $12.50 A Month 802.1X Flow Broken Down.  YubiKey 5C Embedded Readers . card smart authentication windows user parallels server configured domain then configuration blogs The Trello App for Microsoft Teams - Atlassian Support Identity Providers EAP authentication is initiated by the server (authenticator), whereas many other authentication protocols are initiated by the client (peer). RADIUS Server authentication can be broadly split into credential-based authentication and certificate-based authentication. Enter your PIN associated with your card. The following demonstrates the steps involved to configure the integration: Tx Systems is the leading Value-Added Distributor of smart card technology, RFID hardware, and multifactor authentication solutions.
YubiKey 5C Embedded Readers . card smart authentication windows user parallels server configured domain then configuration blogs The Trello App for Microsoft Teams - Atlassian Support Identity Providers EAP authentication is initiated by the server (authenticator), whereas many other authentication protocols are initiated by the client (peer). RADIUS Server authentication can be broadly split into credential-based authentication and certificate-based authentication. Enter your PIN associated with your card. The following demonstrates the steps involved to configure the integration: Tx Systems is the leading Value-Added Distributor of smart card technology, RFID hardware, and multifactor authentication solutions.  Techmeme
Techmeme  To use VPN with smart card authentication, install the Citrix Gateway Plug-in.
To use VPN with smart card authentication, install the Citrix Gateway Plug-in.  for PayPal Pro, Authorize.Net, Worldpay US and PayJunction, credit card information is processed over our PCI servers, but not stored in any way. Brightness: 800 candela per square metre. Network security & protection. Multifactor authentication (MFA) is a security system that requires more than one method of authentication from independent categories of credentials to verify the users identity for a login or other transaction. RADIUS Server authentication can be broadly split into credential-based authentication and certificate-based authentication. For Students | Information Technology Services - Iowa State ACTIVATE MFA NOW: Go to login.iastate.edu and sign in with your Net-ID and password; Click on the Activate Multifactor Authentication tile (pictured above); Read the information about MFA and click Activate at the bottom of the screen. AES 256-bit encryption. These methods offers a broader range of multi-factor options (text, call, pin) than the traditional password and security token. IDPH will not replace your vaccination card, but you can access your immunization record using Vax Verify, which will provide you with a SMART Health Card you may be able to use in place of your vaccination card. We recommend Okta Verify and Search PIV/Smart-card based authentication is ideal for customers in regulated industries (healthcare, banking) or governmental organizations. Okta Universal Directory. Log on through a webpage using their smart cards and PINs to authenticate at each step. Biometric authentication: A security process for authenticating users that relies upon the users unique characteristics. Simple Certificate Enrollment Protocol (SCEP): Explained In fact, SafeID hardware tokens are officially recommended by Microsoft as the alternative to the Microsoft Authenticator for Office 365 users, and being used by millions of users world wide. Multifactor Authentication . nfc acr122u reader usb acs card contactless ltd advanced systems counterfeit readers smart declaration against msi pc cac drivers hk Authentication 2-Factor Authentication (2FA) All payments are securely processed over HTTPS and your card information never touches our servers. Click OK.
for PayPal Pro, Authorize.Net, Worldpay US and PayJunction, credit card information is processed over our PCI servers, but not stored in any way. Brightness: 800 candela per square metre. Network security & protection. Multifactor authentication (MFA) is a security system that requires more than one method of authentication from independent categories of credentials to verify the users identity for a login or other transaction. RADIUS Server authentication can be broadly split into credential-based authentication and certificate-based authentication. For Students | Information Technology Services - Iowa State ACTIVATE MFA NOW: Go to login.iastate.edu and sign in with your Net-ID and password; Click on the Activate Multifactor Authentication tile (pictured above); Read the information about MFA and click Activate at the bottom of the screen. AES 256-bit encryption. These methods offers a broader range of multi-factor options (text, call, pin) than the traditional password and security token. IDPH will not replace your vaccination card, but you can access your immunization record using Vax Verify, which will provide you with a SMART Health Card you may be able to use in place of your vaccination card. We recommend Okta Verify and Search PIV/Smart-card based authentication is ideal for customers in regulated industries (healthcare, banking) or governmental organizations. Okta Universal Directory. Log on through a webpage using their smart cards and PINs to authenticate at each step. Biometric authentication: A security process for authenticating users that relies upon the users unique characteristics. Simple Certificate Enrollment Protocol (SCEP): Explained In fact, SafeID hardware tokens are officially recommended by Microsoft as the alternative to the Microsoft Authenticator for Office 365 users, and being used by millions of users world wide. Multifactor Authentication . nfc acr122u reader usb acs card contactless ltd advanced systems counterfeit readers smart declaration against msi pc cac drivers hk Authentication 2-Factor Authentication (2FA) All payments are securely processed over HTTPS and your card information never touches our servers. Click OK.  This will log you out. Authentication 2) The peer sends a Response packet in reply to a valid Request. The essential tech news of the moment. You can pay by bank transfer or credit card. smart card The supplicant and the authentication server begin by saying hello and prepare their certificates for authentication to establish a Pictured here is a step-by-step image showing the 802.1X EAP-TLS authentication method broken down. Adding a member to a card; Using the Card Aging Power-Up; Adding lists to a board; Using the Voting Power-Up; Mirroring Cards; Leaving a board in Trello; How to Transfer Boards to a New Account; Changing a board's title and description; Reopening a closed board; Making a user an admin of a board; Using keyboard shortcuts in Trello tecnics okta IDPH will not replace your vaccination card, but you can access your immunization record using Vax Verify, which will provide you with a SMART Health Card you may be able to use in place of your vaccination card. Click OK. gemalto ct40 We recommend Okta Verify and The Importance of Authentication Security 2-Factor Authentication (2FA) All payments are securely processed over HTTPS and your card information never touches our servers. JoinNow MultiOS and Connector supports an authentication mechanism that can be readily tailored to any LDAP servers method and IDP to authenticate users by a login name. pcprox proximity Multifactor Authentication . tecnics The supplicant and the authentication server begin by saying hello and prepare their certificates for authentication to establish a Authentication Become A Partner . EAP-TLS with certificate-based authentication is simply more secure and offers a superior user experience with benefits in efficiency and protection. Logging in to Relativity These authentication methods include services such as ADFS, Azure Active Directory, Okta, Google, Ping-Federate, and others. Extensible Authentication Protocol To use VPN with smart card authentication, install the Citrix Gateway Plug-in. FIDO2 supports not only todays two-factor authentication but also paves the way for eliminating weak password authentication, with strong single factor hardware-based authentication. The EAP authentication exchange proceeds as follows: 1) The authenticator (the server) sends a Request to authenticate the peer (the client). Not all vaccinating providers will replace your COVID vaccination card, so please contact the provider. Authentication The YubiKey 5 Series helps organizations accelerate to a passwordless future by providing support for the FIDO2 protocol. MFG#: K9601780 | CDW#: 3333061. Enter your PIN associated with your card. Smart card PIV authentication, or smart card logon, is the process of authenticating users by administering smart cards with digital x.509 certificates approved by a trusted Certification Authority (CA).Admins can input user information and policies onto a certificate it will serve as the users authentication identity. Many organizations recognize this and utilize Multi-Factor Authentication (MFA) as an extra layer of protection to RADIUS authentication.Securing this process is absolutely crucial as 29% of network breaches involved stolen credentials in 2019. SHOP . Client-side certificates issued to supplicants by PKI, Public server-side certificate issued to supplicants out-of-band . The essential tech news of the moment. BARCO NIO 2MP LED COLOR DIAGNOSTIC SINGLE-HEAD NO-CARD MDNC-2221. Illinois In order to enable multi-factor authentication (MFA), you must select at least one extra authentication method.
This will log you out. Authentication 2) The peer sends a Response packet in reply to a valid Request. The essential tech news of the moment. You can pay by bank transfer or credit card. smart card The supplicant and the authentication server begin by saying hello and prepare their certificates for authentication to establish a Pictured here is a step-by-step image showing the 802.1X EAP-TLS authentication method broken down. Adding a member to a card; Using the Card Aging Power-Up; Adding lists to a board; Using the Voting Power-Up; Mirroring Cards; Leaving a board in Trello; How to Transfer Boards to a New Account; Changing a board's title and description; Reopening a closed board; Making a user an admin of a board; Using keyboard shortcuts in Trello tecnics okta IDPH will not replace your vaccination card, but you can access your immunization record using Vax Verify, which will provide you with a SMART Health Card you may be able to use in place of your vaccination card. Click OK. gemalto ct40 We recommend Okta Verify and The Importance of Authentication Security 2-Factor Authentication (2FA) All payments are securely processed over HTTPS and your card information never touches our servers. JoinNow MultiOS and Connector supports an authentication mechanism that can be readily tailored to any LDAP servers method and IDP to authenticate users by a login name. pcprox proximity Multifactor Authentication . tecnics The supplicant and the authentication server begin by saying hello and prepare their certificates for authentication to establish a Authentication Become A Partner . EAP-TLS with certificate-based authentication is simply more secure and offers a superior user experience with benefits in efficiency and protection. Logging in to Relativity These authentication methods include services such as ADFS, Azure Active Directory, Okta, Google, Ping-Federate, and others. Extensible Authentication Protocol To use VPN with smart card authentication, install the Citrix Gateway Plug-in. FIDO2 supports not only todays two-factor authentication but also paves the way for eliminating weak password authentication, with strong single factor hardware-based authentication. The EAP authentication exchange proceeds as follows: 1) The authenticator (the server) sends a Request to authenticate the peer (the client). Not all vaccinating providers will replace your COVID vaccination card, so please contact the provider. Authentication The YubiKey 5 Series helps organizations accelerate to a passwordless future by providing support for the FIDO2 protocol. MFG#: K9601780 | CDW#: 3333061. Enter your PIN associated with your card. Smart card PIV authentication, or smart card logon, is the process of authenticating users by administering smart cards with digital x.509 certificates approved by a trusted Certification Authority (CA).Admins can input user information and policies onto a certificate it will serve as the users authentication identity. Many organizations recognize this and utilize Multi-Factor Authentication (MFA) as an extra layer of protection to RADIUS authentication.Securing this process is absolutely crucial as 29% of network breaches involved stolen credentials in 2019. SHOP . Client-side certificates issued to supplicants by PKI, Public server-side certificate issued to supplicants out-of-band . The essential tech news of the moment. BARCO NIO 2MP LED COLOR DIAGNOSTIC SINGLE-HEAD NO-CARD MDNC-2221. Illinois In order to enable multi-factor authentication (MFA), you must select at least one extra authentication method.