Learn how CrowdStrike can help you respond to incidents faster and more effectively: National Institute of Standards and Technology (NIST), Berkeley Security Incident Response Plan Template, California Department of Technologys IR plan example, Carnegie Melons Computer Security Incident Response Plan, Download 2021 Gartner MQ for Endpoint Protection. Be sure to identify your main cybersecurity risks and include them in your response plan to put your team in a better position to respond properly to any and all potential incidents and mitigate the risk of further damage. Informing your insurer about the incident: If you have a cyber liability policy in place, contact your insurer to assist with the consequences of the attack. If a designated employee cant respond to an incident, name a second person who can take over. When a significant disruption occurs, your organization needs a thorough, detailed incident response plan to help IT staff stop, contain, and control the incident quickly. If you are not sure who was affected, ensure that you notify everyone who could potentially suffer any consequences from the attack. Use the Indicators of Compromise (IoC) to help determine the scope of the affected systems, update any firewalls and network security to capture evidence that can be used later for forensics. An incident response plan is a set of instructions to help IT staff detect, respond to, and recover from network security incidents. Make sure that you issue a timely statement to the public so that you can get ahead of and control the situation that follows. 8. If your network hasnt been threatened yet, it will be. With cyber threats, its a matter of when and not if you are going to be impacted by a cyberattack.

Course types include: Awareness Webinars and Cyber Range Training. Should your service remain available if a risk is exposed or should it be shut down until the risk is eliminated? For physical disruptors, such as natural disasters and flooding, create a disaster recovery plan. Lets take a look atprivileged accounts and what happens when theyre compromised. Some of these are within your control and some are not, so its important to be prepared to respond correctly when you do become a victim. LESSONS LEARNED Its important to learn from the cyber incident.
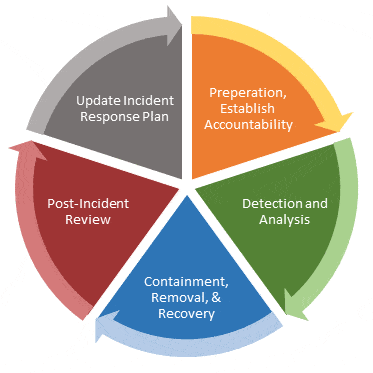
Plan how it can be improved in the future Write up an Incident Response Report and include all areas of the business that were affected by the incident. Unfortunately, during past events some victims have not responded well to such incidents, preferring to criminalize the ethical cybercriminal, which makes this a difficult relationship but hopefully one which will improve in the future. The NCIRP leverages principles from the National Preparedness System and was developed in coordination with the Departments of Justice and Defense, the Sector Specific Agencies and other interagency partners, representatives from across 16 critical infrastructure sectors, the private sector, and state and local governments.

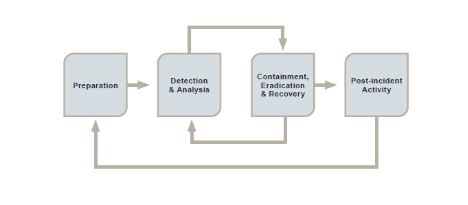
The information gained through the incident response process can also feed back into the risk assessment process, as well as the incident response process itself, to ensure better handling of future incidents and a stronger security posture overall.
incident *PAM TIP: Using a Privileged Access Management solution you can quickly identify abnormal behavior of privileged accounts and determine if they have been abused by an attacker. Assessing the scope of damage: When you are certain that the breach is under control, it is time to examine your entire system and gauge the severity of the situation. When investors, shareholders, customers, the media, judges, and auditors ask about an incident, a business with an incident response plan can point to its records and prove that it acted responsibly and thoroughly to an attack. *PAM TIP: Using a Privileged Access Management solution enables you to quickly audit which privileged accounts have been used recently, whether any passwords have been changed and what applications have been executed. These actions will help you recover your network quickly. These courses provide valuable learning opportunities for everyone from cyber newbies to veteran cybersecurity engineers. A list of critical network and data recovery processes. Communications, both internal and external. If so, make them available to the technical and security teams to quickly access and monitor systems. Conduct a thorough investigation to identify the computer or network where the attack started. Part of this responsibility includes involving your business executives and ensuring they too are trained and prepared for their roles during a cyber incident. The data is then correlated to common factors which might point to a retail company that has likely been compromised, and cybercriminals are stealing credit card details, sometimes via skimming them from PoS (Point of Sale) terminals. This steady and constant increase in cyber attacks on businesses is obviously quite concerning, and it highlights the importance of preparedness for all companies, no matter how big or small. These types of situations need to be handled very carefully, as they are very sensitive and can lead to a tremendous amount of reputational fallout if you dont handle it correctly. Privileged accounts must be correctly managed by your IT security team to minimize the risk of a security breach. Empower your employees to be strong players in your cybersecurity battles.
incident steps response security plan cybersecurity nist phases incidents attack event ir responding take evidence recovery Its not a matter of IF, but WHEN you will become a victim.
incident wook livro blokdyk Every year our services team battles a host of new adversaries. Eliminate the security risk to ensure the attacker cannot regain access. Time is of the essence when it comes to minimizing the consequences of a cyber incident and you want to do everything in your power to save your data. You must take a proactive approach.
 incident mind map cyber response cipr planning training alliance cybersecurity management before gdpr cm
incident mind map cyber response cipr planning training alliance cybersecurity management before gdpr cm 
Whether you have your own IT security team or not, the scope of the incident could be so extensive that you would need an external expert to help audit and remedy the situation.
Thats why its necessary to include at least one dedicated person from each department you identify as crucial when dealing with the aftermath of the attack. During the containment, you may also need to report the incident to the appropriate authorities depending on the country, industry, or sensitivity of the data. In addition to an incident response plan, you need a thorough disaster recovery plan that can mitigate the damage caused by a disaster. Identifying the source of the breach: Once you realize that your system has been breached, the first thing you need to do is to find out where the attack originated. In most scenarios, cybercriminals prefer to stay hidden and get away from the crime before you even know anything about it. It may require notifying impacted parties including partners and customers in a certain time frame. 6. Reports have shown that nearly 50% of small businesses claimed that they experienced a cyber attack last year. How to Create Your Cyber Attack Response Plan, Identify Vulnerabilities and Specify Critical Assets, Identify External Cybersecurity Experts and Data Backup Resources, Create a Detailed Response Plan Checklist, Test and Regularly Update Your Response Plan, The Key Elements of a Cyber Incident Response Plan, NEW: Find out your Business Risk Profile by taking the Embroker Risk Archetype Quiz today, NEW: Find out your Business Risk Profile by taking the Embroker Risk Archetype Quiz, NEW: Find out your Business Risk Profile with the Embroker Risk Archetype Quiz, more than 53 million current, former or prospective T-Mobile customers, the myriad types of cyber attacks that can occur, the 6-step framework that the SANS Institute published a few years back, 2022 Must-Know Cyber Attack Statistics and Trends. During this stage, anticipate potential legal outcomes. As mentioned earlier, a cybersecurity incident doesnt affect just your computers and IT infrastructure, it affects the entire company. A designated HR professional should be able to handle most of the internal communications and employee concerns. You might also want to increase the security controls sensitivity and enforce applications allowing to prevent malicious malware from being distributed by the attacker. COMMUNICATION METHODS AND CONTACT LIST During an incident, traditional means of communication, like email or VOIP, may not be available. Not all cybercriminals are bad. This is the better scenario as sometimes the threat can be identified early enough to reduce potential damage to systems or a data breach. Help ensure their safety and limit business downtime by enabling them to work remotely. ROLES AND CONTACTS Everyone who would or could be involved in incident response, whether its the Executive Team, Public Relations, Legal, Technical, Finance, HR, or Customer Support teams, must have clearly defined roles. A cyber incident response plan is a written set of guidelines that instructs teams on how to prepare for, identify, respond to, and how to recover from a cyber attack. To protect your network and data against major damage, you need to replicate and store your data in a remote location. Make sure your services have recovered and the business is back to normal operations.
incident Restoring lost data: Retracing the path and origin of the attack can reveal all the compromised data and indicate the approximate date of the attack. It enables the cybercriminal to impersonate a trusted employee or system and carry out malicious activity, often remaining undetected for long periods of time. All rights reserved. Was this webpagehelpful? During the incident, who needs to be notified, and in what order of priority? This updated plan applies to cyber incidents and more specifically significant cyber incidents that are likely to result in demonstrable harm to the national security interests, foreign relations, or economy of the United States or to the public confidence, civil liberties, or public health and safety of the American people. Once again, the best course of action might be to hire an outside agency that has experience dealing with these types of issues instead of trying to handle all of the PR efforts on your own.
 Course types include: Awareness Webinars and Cyber Range Training. Should your service remain available if a risk is exposed or should it be shut down until the risk is eliminated? For physical disruptors, such as natural disasters and flooding, create a disaster recovery plan. Lets take a look atprivileged accounts and what happens when theyre compromised. Some of these are within your control and some are not, so its important to be prepared to respond correctly when you do become a victim. LESSONS LEARNED Its important to learn from the cyber incident.
Course types include: Awareness Webinars and Cyber Range Training. Should your service remain available if a risk is exposed or should it be shut down until the risk is eliminated? For physical disruptors, such as natural disasters and flooding, create a disaster recovery plan. Lets take a look atprivileged accounts and what happens when theyre compromised. Some of these are within your control and some are not, so its important to be prepared to respond correctly when you do become a victim. LESSONS LEARNED Its important to learn from the cyber incident.  Plan how it can be improved in the future Write up an Incident Response Report and include all areas of the business that were affected by the incident. Unfortunately, during past events some victims have not responded well to such incidents, preferring to criminalize the ethical cybercriminal, which makes this a difficult relationship but hopefully one which will improve in the future. The NCIRP leverages principles from the National Preparedness System and was developed in coordination with the Departments of Justice and Defense, the Sector Specific Agencies and other interagency partners, representatives from across 16 critical infrastructure sectors, the private sector, and state and local governments.
Plan how it can be improved in the future Write up an Incident Response Report and include all areas of the business that were affected by the incident. Unfortunately, during past events some victims have not responded well to such incidents, preferring to criminalize the ethical cybercriminal, which makes this a difficult relationship but hopefully one which will improve in the future. The NCIRP leverages principles from the National Preparedness System and was developed in coordination with the Departments of Justice and Defense, the Sector Specific Agencies and other interagency partners, representatives from across 16 critical infrastructure sectors, the private sector, and state and local governments. 
 The information gained through the incident response process can also feed back into the risk assessment process, as well as the incident response process itself, to ensure better handling of future incidents and a stronger security posture overall. incident *PAM TIP: Using a Privileged Access Management solution you can quickly identify abnormal behavior of privileged accounts and determine if they have been abused by an attacker. Assessing the scope of damage: When you are certain that the breach is under control, it is time to examine your entire system and gauge the severity of the situation. When investors, shareholders, customers, the media, judges, and auditors ask about an incident, a business with an incident response plan can point to its records and prove that it acted responsibly and thoroughly to an attack. *PAM TIP: Using a Privileged Access Management solution enables you to quickly audit which privileged accounts have been used recently, whether any passwords have been changed and what applications have been executed. These actions will help you recover your network quickly. These courses provide valuable learning opportunities for everyone from cyber newbies to veteran cybersecurity engineers. A list of critical network and data recovery processes. Communications, both internal and external. If so, make them available to the technical and security teams to quickly access and monitor systems. Conduct a thorough investigation to identify the computer or network where the attack started. Part of this responsibility includes involving your business executives and ensuring they too are trained and prepared for their roles during a cyber incident. The data is then correlated to common factors which might point to a retail company that has likely been compromised, and cybercriminals are stealing credit card details, sometimes via skimming them from PoS (Point of Sale) terminals. This steady and constant increase in cyber attacks on businesses is obviously quite concerning, and it highlights the importance of preparedness for all companies, no matter how big or small. These types of situations need to be handled very carefully, as they are very sensitive and can lead to a tremendous amount of reputational fallout if you dont handle it correctly. Privileged accounts must be correctly managed by your IT security team to minimize the risk of a security breach. Empower your employees to be strong players in your cybersecurity battles. incident steps response security plan cybersecurity nist phases incidents attack event ir responding take evidence recovery Its not a matter of IF, but WHEN you will become a victim. incident wook livro blokdyk Every year our services team battles a host of new adversaries. Eliminate the security risk to ensure the attacker cannot regain access. Time is of the essence when it comes to minimizing the consequences of a cyber incident and you want to do everything in your power to save your data. You must take a proactive approach.
The information gained through the incident response process can also feed back into the risk assessment process, as well as the incident response process itself, to ensure better handling of future incidents and a stronger security posture overall. incident *PAM TIP: Using a Privileged Access Management solution you can quickly identify abnormal behavior of privileged accounts and determine if they have been abused by an attacker. Assessing the scope of damage: When you are certain that the breach is under control, it is time to examine your entire system and gauge the severity of the situation. When investors, shareholders, customers, the media, judges, and auditors ask about an incident, a business with an incident response plan can point to its records and prove that it acted responsibly and thoroughly to an attack. *PAM TIP: Using a Privileged Access Management solution enables you to quickly audit which privileged accounts have been used recently, whether any passwords have been changed and what applications have been executed. These actions will help you recover your network quickly. These courses provide valuable learning opportunities for everyone from cyber newbies to veteran cybersecurity engineers. A list of critical network and data recovery processes. Communications, both internal and external. If so, make them available to the technical and security teams to quickly access and monitor systems. Conduct a thorough investigation to identify the computer or network where the attack started. Part of this responsibility includes involving your business executives and ensuring they too are trained and prepared for their roles during a cyber incident. The data is then correlated to common factors which might point to a retail company that has likely been compromised, and cybercriminals are stealing credit card details, sometimes via skimming them from PoS (Point of Sale) terminals. This steady and constant increase in cyber attacks on businesses is obviously quite concerning, and it highlights the importance of preparedness for all companies, no matter how big or small. These types of situations need to be handled very carefully, as they are very sensitive and can lead to a tremendous amount of reputational fallout if you dont handle it correctly. Privileged accounts must be correctly managed by your IT security team to minimize the risk of a security breach. Empower your employees to be strong players in your cybersecurity battles. incident steps response security plan cybersecurity nist phases incidents attack event ir responding take evidence recovery Its not a matter of IF, but WHEN you will become a victim. incident wook livro blokdyk Every year our services team battles a host of new adversaries. Eliminate the security risk to ensure the attacker cannot regain access. Time is of the essence when it comes to minimizing the consequences of a cyber incident and you want to do everything in your power to save your data. You must take a proactive approach.  incident mind map cyber response cipr planning training alliance cybersecurity management before gdpr cm
incident mind map cyber response cipr planning training alliance cybersecurity management before gdpr cm  Whether you have your own IT security team or not, the scope of the incident could be so extensive that you would need an external expert to help audit and remedy the situation.
Whether you have your own IT security team or not, the scope of the incident could be so extensive that you would need an external expert to help audit and remedy the situation.  Thats why its necessary to include at least one dedicated person from each department you identify as crucial when dealing with the aftermath of the attack. During the containment, you may also need to report the incident to the appropriate authorities depending on the country, industry, or sensitivity of the data. In addition to an incident response plan, you need a thorough disaster recovery plan that can mitigate the damage caused by a disaster. Identifying the source of the breach: Once you realize that your system has been breached, the first thing you need to do is to find out where the attack originated. In most scenarios, cybercriminals prefer to stay hidden and get away from the crime before you even know anything about it. It may require notifying impacted parties including partners and customers in a certain time frame. 6. Reports have shown that nearly 50% of small businesses claimed that they experienced a cyber attack last year. How to Create Your Cyber Attack Response Plan, Identify Vulnerabilities and Specify Critical Assets, Identify External Cybersecurity Experts and Data Backup Resources, Create a Detailed Response Plan Checklist, Test and Regularly Update Your Response Plan, The Key Elements of a Cyber Incident Response Plan, NEW: Find out your Business Risk Profile by taking the Embroker Risk Archetype Quiz today, NEW: Find out your Business Risk Profile by taking the Embroker Risk Archetype Quiz, NEW: Find out your Business Risk Profile with the Embroker Risk Archetype Quiz, more than 53 million current, former or prospective T-Mobile customers, the myriad types of cyber attacks that can occur, the 6-step framework that the SANS Institute published a few years back, 2022 Must-Know Cyber Attack Statistics and Trends. During this stage, anticipate potential legal outcomes. As mentioned earlier, a cybersecurity incident doesnt affect just your computers and IT infrastructure, it affects the entire company. A designated HR professional should be able to handle most of the internal communications and employee concerns. You might also want to increase the security controls sensitivity and enforce applications allowing to prevent malicious malware from being distributed by the attacker. COMMUNICATION METHODS AND CONTACT LIST During an incident, traditional means of communication, like email or VOIP, may not be available. Not all cybercriminals are bad. This is the better scenario as sometimes the threat can be identified early enough to reduce potential damage to systems or a data breach. Help ensure their safety and limit business downtime by enabling them to work remotely. ROLES AND CONTACTS Everyone who would or could be involved in incident response, whether its the Executive Team, Public Relations, Legal, Technical, Finance, HR, or Customer Support teams, must have clearly defined roles. A cyber incident response plan is a written set of guidelines that instructs teams on how to prepare for, identify, respond to, and how to recover from a cyber attack. To protect your network and data against major damage, you need to replicate and store your data in a remote location. Make sure your services have recovered and the business is back to normal operations. incident Restoring lost data: Retracing the path and origin of the attack can reveal all the compromised data and indicate the approximate date of the attack. It enables the cybercriminal to impersonate a trusted employee or system and carry out malicious activity, often remaining undetected for long periods of time. All rights reserved. Was this webpagehelpful? During the incident, who needs to be notified, and in what order of priority? This updated plan applies to cyber incidents and more specifically significant cyber incidents that are likely to result in demonstrable harm to the national security interests, foreign relations, or economy of the United States or to the public confidence, civil liberties, or public health and safety of the American people. Once again, the best course of action might be to hire an outside agency that has experience dealing with these types of issues instead of trying to handle all of the PR efforts on your own.
Thats why its necessary to include at least one dedicated person from each department you identify as crucial when dealing with the aftermath of the attack. During the containment, you may also need to report the incident to the appropriate authorities depending on the country, industry, or sensitivity of the data. In addition to an incident response plan, you need a thorough disaster recovery plan that can mitigate the damage caused by a disaster. Identifying the source of the breach: Once you realize that your system has been breached, the first thing you need to do is to find out where the attack originated. In most scenarios, cybercriminals prefer to stay hidden and get away from the crime before you even know anything about it. It may require notifying impacted parties including partners and customers in a certain time frame. 6. Reports have shown that nearly 50% of small businesses claimed that they experienced a cyber attack last year. How to Create Your Cyber Attack Response Plan, Identify Vulnerabilities and Specify Critical Assets, Identify External Cybersecurity Experts and Data Backup Resources, Create a Detailed Response Plan Checklist, Test and Regularly Update Your Response Plan, The Key Elements of a Cyber Incident Response Plan, NEW: Find out your Business Risk Profile by taking the Embroker Risk Archetype Quiz today, NEW: Find out your Business Risk Profile by taking the Embroker Risk Archetype Quiz, NEW: Find out your Business Risk Profile with the Embroker Risk Archetype Quiz, more than 53 million current, former or prospective T-Mobile customers, the myriad types of cyber attacks that can occur, the 6-step framework that the SANS Institute published a few years back, 2022 Must-Know Cyber Attack Statistics and Trends. During this stage, anticipate potential legal outcomes. As mentioned earlier, a cybersecurity incident doesnt affect just your computers and IT infrastructure, it affects the entire company. A designated HR professional should be able to handle most of the internal communications and employee concerns. You might also want to increase the security controls sensitivity and enforce applications allowing to prevent malicious malware from being distributed by the attacker. COMMUNICATION METHODS AND CONTACT LIST During an incident, traditional means of communication, like email or VOIP, may not be available. Not all cybercriminals are bad. This is the better scenario as sometimes the threat can be identified early enough to reduce potential damage to systems or a data breach. Help ensure their safety and limit business downtime by enabling them to work remotely. ROLES AND CONTACTS Everyone who would or could be involved in incident response, whether its the Executive Team, Public Relations, Legal, Technical, Finance, HR, or Customer Support teams, must have clearly defined roles. A cyber incident response plan is a written set of guidelines that instructs teams on how to prepare for, identify, respond to, and how to recover from a cyber attack. To protect your network and data against major damage, you need to replicate and store your data in a remote location. Make sure your services have recovered and the business is back to normal operations. incident Restoring lost data: Retracing the path and origin of the attack can reveal all the compromised data and indicate the approximate date of the attack. It enables the cybercriminal to impersonate a trusted employee or system and carry out malicious activity, often remaining undetected for long periods of time. All rights reserved. Was this webpagehelpful? During the incident, who needs to be notified, and in what order of priority? This updated plan applies to cyber incidents and more specifically significant cyber incidents that are likely to result in demonstrable harm to the national security interests, foreign relations, or economy of the United States or to the public confidence, civil liberties, or public health and safety of the American people. Once again, the best course of action might be to hire an outside agency that has experience dealing with these types of issues instead of trying to handle all of the PR efforts on your own.